Have A Virus Scanner Recommendations For Mac
The differences between Mac and PC computers are generally well-understood by this point in the Platform Wars. One of the prime selling points for Macintosh has traditionally been its relative immunity from computer viruses. Unfortunately, however, that changed recently when a Trojan virus called Flashback attacked more than 500,000 Macs.
Unhappy Mac’s (and Mac users) are fighting the Flashback virus. And although it was pretty much a first-time occurrence, it was an event that’s now giving Mac users plenty of cause for concern. As a public service to those Mac users, we’re offering the following tips on how to find out if your Mac is hosting the Flashback virus, and what to do about it if your computer is infected.
Know Your Enemy: How to Find Out if Your Mac Has a Virus Flashback (which spreads malware) is a very insidious virus, partly because it can get under your computer’s skin even without first gaining an administrative password. It gets “in” by targeting a weakness in Java. That’s not news to Oracle, Java’s creators, which has been proactive in dealing with the matter.
In February, Oracle came up with a fix for the Java problem. And that would have taken care of Flashback altogether, except for the fact that Apple has its own version of Java and Oracle’s patch would not solve the problem for Apple’s version. And although Apple got its own patch out recently, there was a time delay that gave Flashback the chance to do its worst. Consequently, the die had already been cast for a half million Mac users, whose machines became infected with malware initiated by Flashback. Section 1: Running Diagnostic Tests First things first: You need to determine if your CPU is carrying the virus. The quickest and best way to do this is to use Kaspersky Lab’s.
But there is one caveat to following this method: you must first know the universally unique identifier (UUID) for your particular Mac. Don’t worryFortunately, finding your UUID is a painless process How to Find Your UUID. Go to Finder and choose the menu item called “About This Mac.”. Next, locate the “More info” option and select that. In the next window you see, locate “Hardware UUID.”. Copy the Hardware UUID, which is a lengthy series of 32 numerals and letters. In the event you’re running a MacBook Air, the procedure for locating the UUID is roughly the same:.
Go to Finder and choose the menu item called “About This Mac.”. Next, press the button labeled “System Report.”. Within the Hardware Overview, you’ll find the UUID. Copy the Hardware UUID to your clipboard. At this point, if you’ve got the UUID, you’re pretty much set. All you need to do is go to, follow the prompts and enter the UUID when requested. Flashbackcheck will then tell you whether or not your computer is carrying the virus.
There are also other ways to find out if your Mac has the virus, if you don’t like the idea of giving a sensitive piece of data (such as the UUID) to an external website. Option 1: Download FlashbackChecker onto your Mac and then simply run the program. Option 2: If you don’t like Option 1, you can also find out if your machine is infected by using your Mac’s Terminal app. This isn’t terribly complicated but does require some additional maneuvers. Go to your Applications folder. Open the Terminal application. Paste the following line of code within Terminal: defaults read /.MacOSX/environment DYLDINSERTLIBRARIES.
Hopefully, you’ll get the following response: The domain/default pair of (/Users//.MacOSX/environment, DYLDINSERTLIBRARIES) does not exist. The key words you’re looking for are “does not exist.” If you get that message, you can relax because it means your Mac is not carrying the Flashback virus. If you don’t get that message, don’t worrybut your machine is probably infected. Assuming you’re not infected, let’s run a double check to make sure your CPU is clean. Type and run this line of code: defaults read /Applications/Safari.app/Contents/Info LSEnvironment.
With any luck you’ll again receive a message saying that it “does not exist.”. As a further check, type in: defaults read /Applications/Firefox.app/Contents/Info LSEnvironment. Once more, you should see a “does not exist” response. If so, go on about your business, because your Mac is clean. On the other hand, if you don’t get that message, move on to our next section.
Get ready to squash some bugs with our step-by-step virus removal instructions. Section 2: Removing the Virus If you’re still reading, we’ll assume that our diagnostic testing has revealed that your machine is indeed infected with Flashback. Here again you have a couple of options you can follow in order to eradicate the menace. As before, the easiest way is to let the pros handle it. There is a special app created by Kaspersky Lab that can manage the entire operation. All you have to do to follow this method is to download the app (which is called the ) and then run it on your system. When you’ve done so, your machine should be clean as a whistlealthough it wouldn’t hurt to re-run the diagnostic procedure we’ve already performed so you can confirm that Flashback’s gone.
For the more adventurous DIY types among you, we’ve got a procedure you can use, although it comes with a warning: If you’re not a skilled computer user who is comfortable working with CPU’s operating system, it may be better to use the Flashfake Removal Tool. (Otherwise you could casually derail your system by entering something incorrectly in your Mac’s command line.) Still with us? Good, let’s go:.

Within the Terminal app, type and run this command: defaults read /Applications/Safari.app/Contents/Info LSEnvironment. Notice the value given with the response “DYLDINSERTLIBRARIES.” Is there only one entry here? (You’ll need to use this info later.).
In the event you then receive an error message stating: “The domain/default pair of (/Applications/Safari.app/Contents/Info, LSEnvironment) does not exist,” move directly to Step 8. Provided you didn’t receive the error message mentioned in Step 3, type and run this command within Terminal: grep -a -o’ldpath-.’%pathobtainedinstep2%. Notice the value given after “ldpath”. (You’ll need to use this info later.). Provided you only saw one entry back in Step 2, you’re ready to type these commands, still within the Terminal app: sudo defaults delete /Applications/Safari.app/Contents/Info LSEnvironment sudo chmod 644 /Applications/Safari.app/Contents/Info/plist. Remember back in Steps 2 and 5 when we asked you to notice the values (files)?
Now you should delete those files. In Terminal, type this command and run it: defaults read /.MacOSX/environment DYLDINSERTLIBRARIES. Now at this point, you may see the following: “The domain/default pair of (/Users/joe/.MacOSX/environment, DYLDINSERTLIBRARIES) does not exist”. If this is the case, congrats! On the other hand, if you don’t get the message, keep pressing on with the rest of our steps, and take note of whatever file information is specified.
(You’ll need this info later.). Within Terminal, type and run this command: grep -a -o’ldpath-.’%pathobtainedinstep9%.
Notice the value given after “ldpath”. (You’ll need to use this info soon.). Still within Terminal, type and run these commands: defaults delete /.MacOSX/environment DYLDINSERTLIBRARIES launchctl unsetenv DYLDINSERTLIBRARIES. Take those files you got in Steps 9 and 11 and delete them. In Terminal, type and run this command: ls -lA /Library/LaunchAgents/. Notice the file name displayed and remember it for later use. If you have one file, move on to the remaining final steps.
(However, if you don’t see a file name displayed, go ahead and contact Customer Support so a trained tech can help you finish up the procedure.). In Terminal, type this command: defaults read /Library/LaunchAgents/%filenameobtainedinstep15% ProgramArguments. Notice the path, which you’ll need during the final step. Does the file name begin with this: “.”? If so, you’re probably no longer infected. Otherwise, proceed to Step 18.
Delete the files you got during Steps 15 and 17. And that should just about do it. To repeat, it’s our recommendation that instead of stepping through a fairly tricky computer procedure, you check out the offerings from Kaspersky Lab. Both Flashbackcheck.com and the Flashfake Removal Tool are designed expressly to keep you from having to monkey around with your computer’s core functionality. But either way, now you should be able to resume your normal Mac activities, secure in the knowledge that all manner of malicious malware isn’t working away, deep within your computer. Finally, it’s important to note that if you own a Mac, you’re probably going to need to take some proactive measure to defend the machine against Flashback.
Virus Scan For Mac Computers
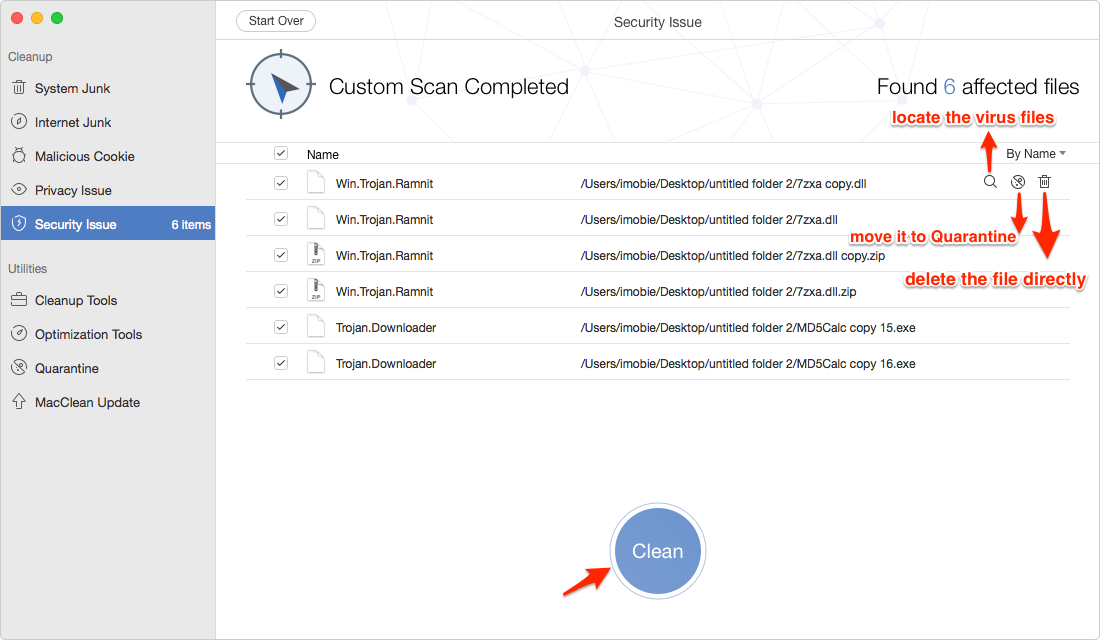
Because the usual antivirus utilities won’t sniff this particular virus out, so it’s up to you to remain on guard. Keeping Your Computer Heathly The world of computing is constantly evolving. Learning more about computers and the code that makes them run can not only be a lifesaver when you’re trying to keep your computer healthy but it can also be a life changing career. Or for example, these programming languages power smartphones, ATMs and a whole host of other electronic devices. Get the skills to fight the hackers – and squash nasty bugs like the Flashback virus too, while you’re at it. SIGN IN TO LEAVE A COMMENT – or – SHARE THIS ARTICLE WITH OTHERS.